Description of the course
The course provides students with knowledge and skills in information systems security controls from a physical and environmental perspective, application, and operation. It focuses on existing types of security controls for organization of information systems, including methodologies, procedures, and implementation design. Students are also introduced to solving security problems in information systems by using different methods, procedures, and controls. They are also taught to apply ethical values for each information security system development to comply with laws and policies for effective control.
Description of the participants
The course is an elective offered by the Faculty of Computer Science and Information Technology under the Department of Information Systems. Participants are enrolled in the Information Technology program of the Faculty of Computer Science. A total of 24 students attended the course in semester 2 of academic year 2022 – 2023.
Description of gamified design thinking activities
Design thinking was used to help students in their continuous assessment in the context of project-based learning. Students worked on a semester-long project. The project objectives were to:
- Explore the current issues of information security in different sectors.
- Determine possible improvements to solve the determined problems in each sector selected.
- Ideate the improvement via a prototype to show its functionality and capability.
Students worked in teams of 4 individuals. A total of 6 groups were formed.
Students were allowed to explore any technology-related design tools, video, editing, and analytic concept to help them answer each of the design thinking phases. For the discussion session, students were asked to use the ICT-INOV design thinking platform.
Work was organized in the following steps:
Step 1. Team building.
Students worked in teams to select a team name and design a team logo, which they uploaded on the ICT-INOV digital learning platform.
Step 2. Problem discovery.
Students identified problems and gaps in related cybersecurity issues using data collection. They identified advantages and disadvantages, problems, issues, and challenges through a small-scale data collection activity based on a survey. Through the data collection, they identified the requirements to improve the current process or system. This became the baseline for the design of an innovative solution.
Step 2. Definition.
Students identified user needs through a survey, the results of which they visualized in graph. They used the results to identify potential improvements. They further identified the specific problems that they wished to focus on. They discussed the objectives of the proposed innovative solution, the target audience, and the technology to be used in its synthesis.
Step 3. Ideation.
Students proposed solutions to the problem in focus. They provided drawings and illustrations of their ideas. They further tested their ideas for viability.
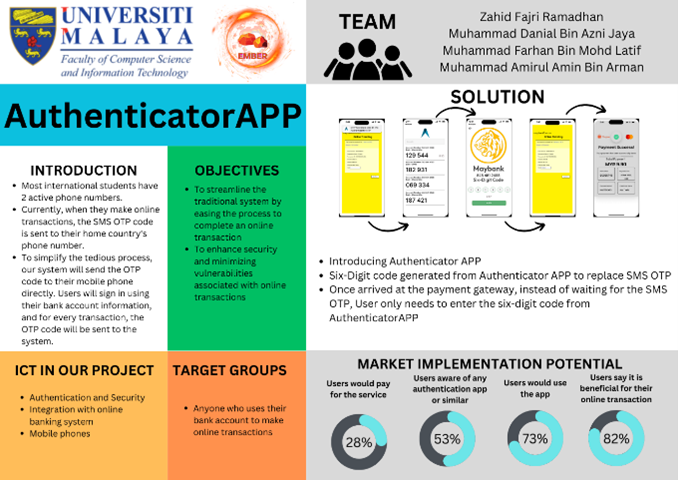
Step 4. Prototyping.
Students developed a prototype for demonstrating their ideas. The prototype was presented in the form of an infographic poster. Students drew and illustrated their innovative product on the poster.
Step 5. Testing.
Students evaluated their prototype with users and developed a short evaluation summary.