Description of the course
The course provides a practical survey of network security applications and standards. It emphasizes applications that are widely used on the internet and for corporate networks. It further emphasizes standards, especially internet standards that have been widely deployed. The course takes placed virtually.
Description of the participants
The course targets students enrolled in the Master’s of Data Science program. In semester 2 of the 2021 – 2022 academic years 67 students attended the course, some of whom were enrolled full-time and some part-time in the Master’s program as they work in parallel with their studies, mostly in the IT field. The course is an elective. The student body was multicultural, with individuals originating from China, Egypt, Bangladesh, Pakistan, Saudi Arabia, Indonesia and Malaysia. Most of the students were in their final year of studies, undertaking their project paper required for their graduation.
Description of gamified design thinking activities
Each student was assigned an individual or group project in cryptography with applications in network security. Active learning was the predominant pedagogical methodology deployed in the course.
Students were encouraged to present their ideas and receive feedback in an interactive session. They further demonstrated their ideas by developing a multimedia prototype using a programming language of their choice.
Activities took place in groups. Group members were jointly responsible for making the project a success. Through the project, students learned how to apply the cryptography techniques, including symmetric, asymmetric, hash and cypher block mode, and presented their findings.
Students engaged in the following steps.
Step 1. Researching mathematical applications for cryptography.
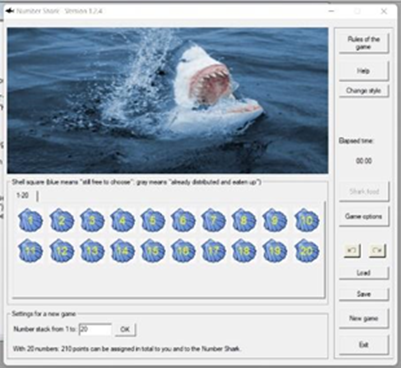
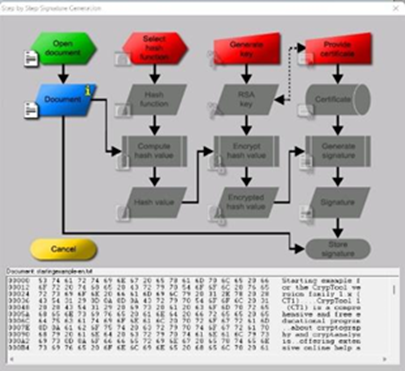
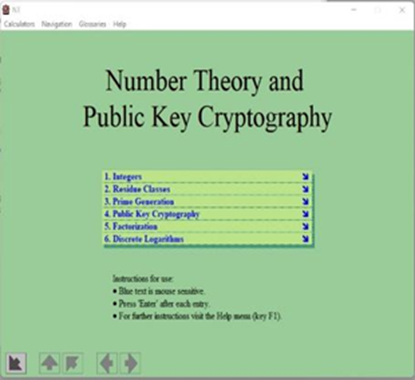
During the 1st part of the educational process students used the Cryptool® application for interactive learning on cryptography. Cryptool® offers 2 interactive games named Number Shark. The purpose of the games was to for the students to understand the concept of prime number factorization of integer numbers, which is mainly used in public key cryptography. More specifically, students selected the size of a shell square. Starting with a minimum of 20 numbers, they gradually increased the size. The biggest shell size supported in the application is 9.999, however solving such a large puzzle would take years. Students were asked to take no more than 3 minutes to finish the 20 number selection. They played against the application and tried to beat the shark. If any of the selected numbers had any real factors, those factors would eaten by the shark. For numbers larger than 100, students typically formed groups of no more than 5 individuals. The game was very useful and enhanced familiarization with prime number selections in RSA and Diffie & Helman public key cryptography. In addition to the Number Shark application, students used interactive tools such as Digital Signature Demonstration and Number Theory Interactive Learning.
Step 2. Researching the state of the art on network security applications.
During the 2nd part of the course students engaged in a group-based active learning project. Students were asked to select recent applications or techniques in network security. Most selected a multimedia application, such as Canva® or any other video editing software, to present their work. The activity encouraged students to creatively present and explain their findings, which contributed to their understanding of network security and to the improvement of their communication skills. Students were given instructions in tutorial sessions in which study questions were introduced. They presented the results of their work using slides and video presentations.
Step 3. Empathy and implementation.
Students worked on assignments, in which they used Cryptool® and Python® to solve problems assigned by the instructor. They worked in groups looking at real-life applications of cryptography. Educators encouraged students to apply empathy by asking them what they believe are the key challenges related to the application of cryptography for network security.
Some of the projects proposed by students include:
- Cyberattack case studies.Case studies on recent cyber-attack in network security and their solutions.
- Social media security. Case studies on social media security challenges and suggested solutions.
- Applications of zero trust networks. Breaking down large networks into smaller ones that do not overlap to minimize the consequences of a corporate network security breach.
- Network security recent issues. Case studies on network security in the modern world and suggested solutions.
- Personal privacy in social networks. Case studies on personal data privacy and suggested solutions.
- Quantum cryptography and its applications. A review on of recent developments in the area.